Hostwinds Tutorials
Search results for:
Table of Contents
WordPress Security and Hardening
WordPress is a top-rated platform for easy-to-use hosting. Being as popular as it introduces many security concerns, however. It is imperative to secure and harden your WordPress installation so that your site remains safe from external attacks. This guide will set forth some basic best practices regarding WordPress security and hardening.
WordPress Security and Hardening
Before we get started, it is important to note that there is no single guide to show you how to make your WordPress bullet-proof. However, this guide aims to teach you to understand better how WordPress works and how it can be vulnerable to certain attacks. Let's start with some basics.
WordPress Core Updates
The very core of the WordPress install requires updates. The maintainers of the core product release updates occasionally to send out features, patches, and security fixes. It is essential to make sure to maintain the newest version of WordPress core. This will ensure the fabric that runs your site itself is as secure as it can be. Keeping WordPress core up to date does not consider plugins, themes, and other useful add-ons. The official WordPress update documentation is a great source to help your WordPress upgrades complete successfully.
Brute Force Attacks
Brute Force is a common cause of compromised WordPress installations. This method attempts to gain access by trying as many username and password combinations as possible in a short period of time. To those that may not understand the process very well, it may seem like a waste of effort. However, computer power and "lists" of common passwords can penetrate the "security" of a simple password in as little as a few minutes. Furthermore, many WordPress installs use the default administrator username of "admin," which further limits how much a remote attacker would need to try. A few easy methods to counter Brute Force attacks are as follows.
- Use a different username for an Administrator account
- High Password Complexity.
- Using a Plugin like Loginizer to prevent excessive login attempts
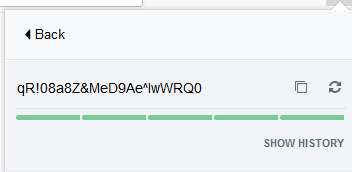
High password complexity can be the difference between a compromised account and a safe account.
Plugin Exploits
WordPress is renowned for its modular and adaptable nature. If you need to add functionality to WordPress, there is likely a plugin ready to enable this. Still, security must be kept in mind when using third-party plugins (and the majority of them are third-party). Third-party plugins can introduce additional methods of penetration (called "Exploits"). This is not always the fault of the plugin creator, but instead may be an incompatibility with other plugins or themes installed. It can also be incompatible with the version of WordPress that you are running. As with many WordPress-related concerns, it is important to keep your plugins up-to-date and do a little legwork to ensure your chosen plugins do not conflict with other plugins already installed. Some tips for keeping your plugins secure include:
- Keep plugins up-to-date
- Vet plugins for reliability
- Browse Plugin Comments
- Disable and Delete unused plugins
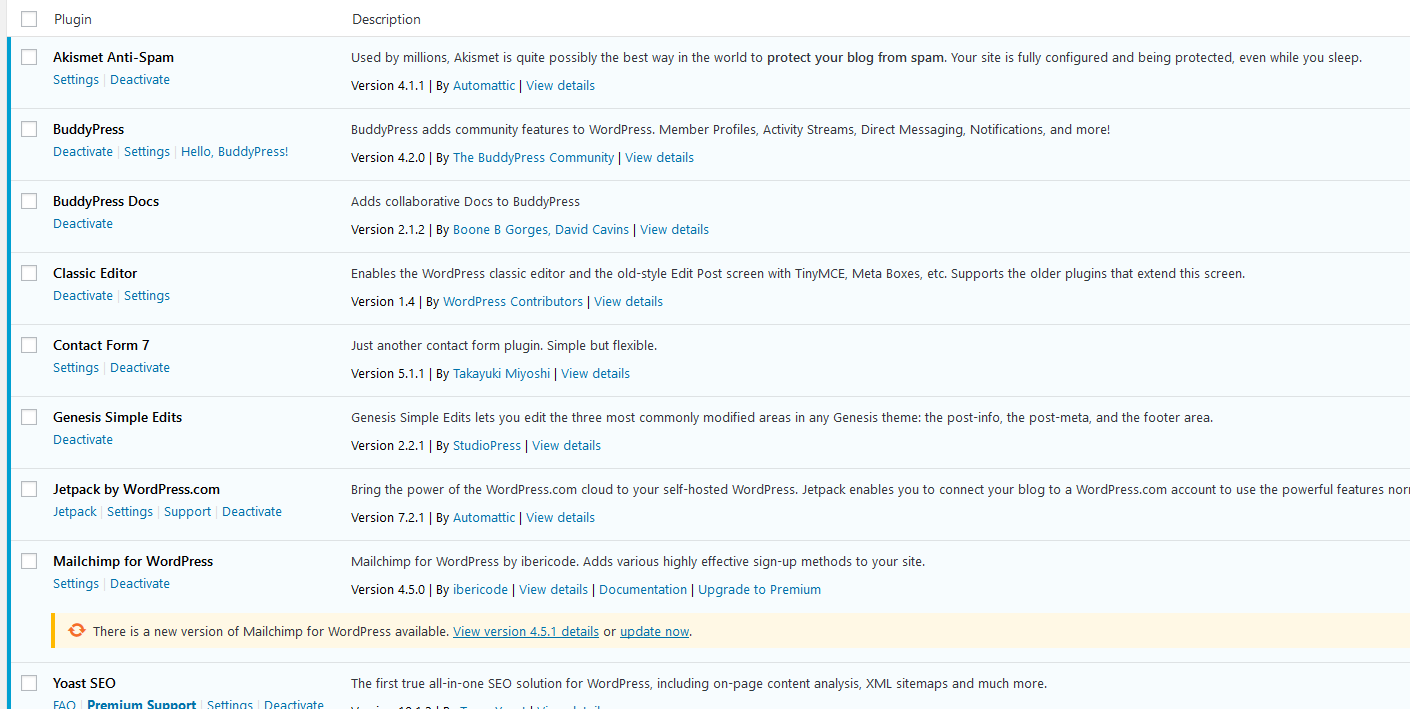
Keeping plugins updated and checking for compatibility is a key component of WordPress security.
SQL Injection Exploits
This guide will not touch on the technical aspects of how this method works. The exploit happens when a form on your WordPress install is not properly configured to handle malformed or malicious submissions. This can allow the attacker to input their own data into sections of your database. This attack attempts to modify your database in a way that changes where your home page or other page leads, called a "redirection."
Protecting your WordPress from this type of attack is simple in practice. Make sure that any forms you insert into your WordPress sanitize their data. That is, it strips any extra data aside from what type of data the firm expects. For instance, when a form asks for a name, non-letter characters are not needed when handling that data. A well-designed form (or plugin that introduces forms into your WordPress) will have good sanitation practices built-in.
General WordPress Security Measures
In some cases, the method in which a WordPress site becomes compromised may not be documented. New exploits and security flaws can surface at any time. There are many ways to ensure that you maintain a secure WordPress install, such as ensuring your site uses HTTPS. Here are some tips to keep your WordPress in good shape, even on the off-chance of a compromise.
Backup Often
The easiest way to recover from a compromised WordPress is to restore from a good and clean backup. However, this requires that you actually have backups available. There are a plethora of tools that make it easy to backup your site daily. Our very own Cloud Backup service for Hostwinds Cloud VPS and Dedicated Servers, as well as Hostwinds Web Hosting Shared Backups, integrates with your server directly. You can include this with your Hostwinds Cloud VPS services, your Hostwinds Dedicated Servers, or your Hostwinds Shared Hosting plans. Alternatively, there are plenty of backup plugins to choose from that have top ratings in the WordPress marketplace. As always, don't forget to vet any plugin you install properly.
Manage Proper Privileges
It is straightforward to overlook this topic. A single-user WordPress site likely doesn't need to worry about this aspect. In multi-user environments, however, it is best practice to provide proper roles that limit permissions. This means only providing the permissions necessary to accomplish any given role. For instance, a user whose sole purpose is to edit drafts wouldn't need access to plugin controls or user modification. Be sure to review the default roles so that you better understand what permissions exist at each level.
Wrapping Up
This guide has gone over a lot of general concepts of WordPress security and hardening practices. This is barely scratching the surface, as there are many fantastic tools and methods available for further securing a WordPress installation. Securing your WordPress is a great step and the first one in a line of other WordPress securing and hardening methods.
Written by Hostwinds Team / April 22, 2019
