Hostwinds Tutorials
Search results for:
Table of Contents
How to Install and Enable Let's Encrypt in WHM/cPanel
Tags: SSL
What is Let's Encrypt?
Let's Encrypt is a Certificate Authority (CA) that provides a free Secure Socket Layer (SSL) certificate to enable verified HTTPS on your website. They will provide you with an SSL Certificate if you can prove domain ownership through the ACME Protocol. The software runs on your web host and verifies the domain is connected to the server. The certificates themselves can be obtained through Let's Encrypt's certbot client or set up through WHM in the AutoSSL configuration page.
Let's Encrypt is only available on our VPS and Dedicated servers. Our Shared, Business, and Reseller hosting benefit from cPanel's automated AutoSSL tool that provides the same type of SSLs with the difference being issued by cPanel powered by Sectigo® instead of Let's Encrypt.
How Do I Enable Let's Encrypt in WHM?
Enabling Let's Encrypt in WHM is actually an easy and seamless process. After logging in to WHM as the root user on your server, click the SSL/TLS icon on the main WHM page, then click Manage AutoSSL. On this page, you can select a provider, and it should display cPanel's default provider and Let's Encrypt. Selecting Let's Encrypt will require that you agree to the terms of use, and it can be done on the Manage AutoSSL page in WHM. Please see the following screenshots for a walkthrough.
Step One: Navigate to the WHM Home Page, click the SSL/TLS icon.

Step Two: Select Manage AutoSSL
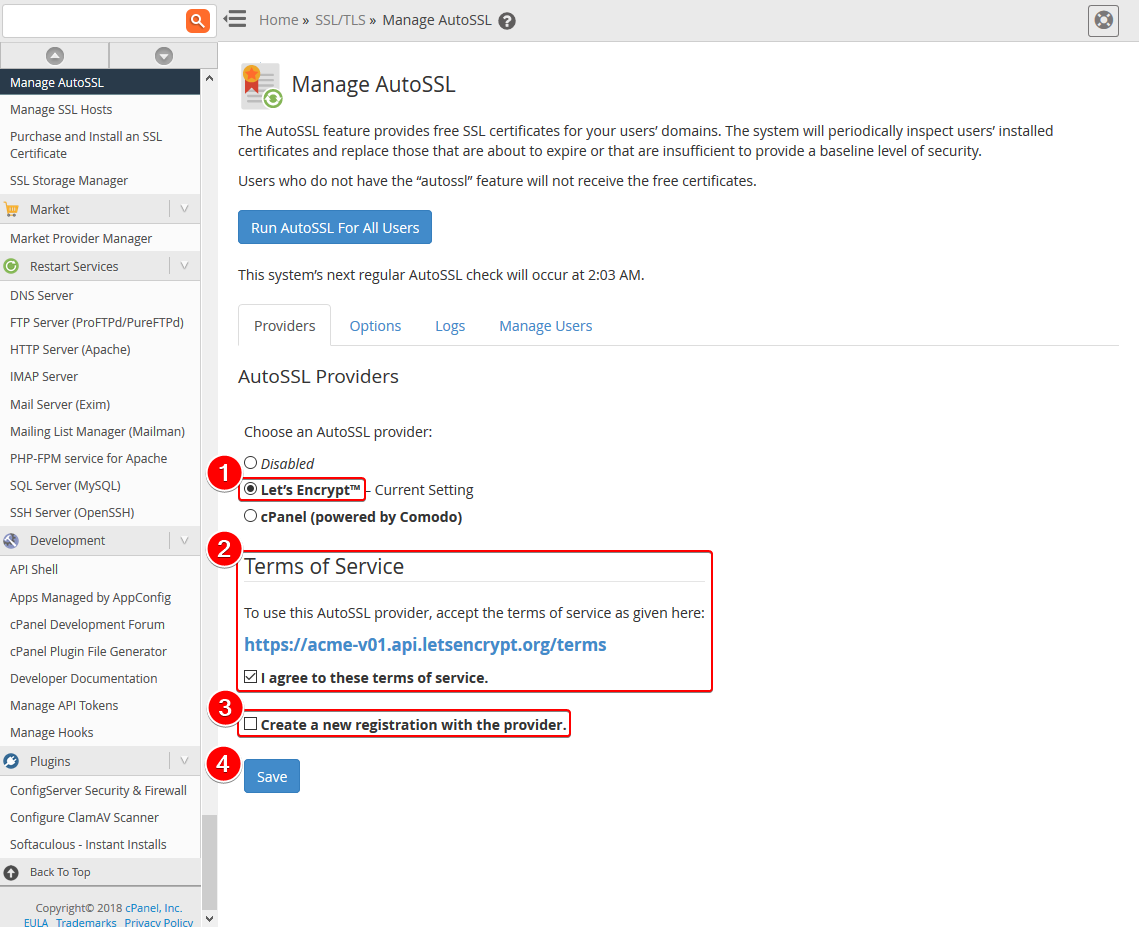
Step Three:
- Select Let's Encrypt from the list of AutoSSL Providers.
- Click the 'I agree to these terms of service.' button after reading the Terms for Let's Encrypt.
- Ensure the box next to 'Create a new registration with the provider.' is unselected.
- Click the Blue Save Button.
If you do not see Let's Encrypt as a provider on this screen, you will need to install the module that allows this. WHM has a built-in script for this. You will need to log into the server over SSH as the root user and run the following command:
/scripts/install_lets_encrypt_autossl_provider
Let's Encrypt imposes significant rate limits, and some features available with cPanel's AutoSSL provider are not available with Let's Encrypt. If you require some of the features cPanel's provider allows, or you are rate limited by Let's Encrypt, you may want to switch back to cPanel's AutoSSL provider.
What About From Inside cPanel?
While the AutoSSL Certificate Provider can only be changed from within WHM, from inside cPanel, you can run the AutoSSL feature manually to help speed up the process of getting an SSL Certificate. We have a guide that can assist with doing this here.
How to Utilize Let's Encrypt on the Linux Command Line
Let's Encrypt provides the certbot software to not only automate the requesting of the certificates but also to integrate the certificates automatically with common web services such as Nginx and Apache. We will cover installation and obtaining your first certificate for CentOS and Ubuntu using the Apache plugin to not only request the certificate but also install the certificate automatically.
Installing On CentOS 7
To utilize Let's Encrypt certificates with Apache on CentOS 7, you'll need to install a couple of things first. This guide assumes you already have at least Apache set up as a web service. Once ready, log into the server over SSH and run the following commands as root.
yum install epel-release
yum install python2-certbot-apache
These commands will install the EPEL (Extended Packages for Enterprise Linux) Release repository, which houses their stable packages, and then install the certbot client with the Apache plugin already installed. Since the packages are now installed, we can continue by setting up your first SSL.
If you are using Nginx as your web server, you can instead run the following commands as the root user,
yum install epel-release
yum install python2-certbot-nginx
Installing On Ubuntu (18.04)
Step One: Add the Certbot PPA repo to the repo list using the following commands,
sudo apt-get update sudo apt-get install software-properties-common sudo add-apt-repository universe sudo add-apt-repository ppa:certbot/certbot sudo apt-get update
Step Two: After those commands have been run and they execute successfully, you will then want to install the certbot software for obtaining the SSL Certificate. This can be done using the following commands:
sudo apt-get install certbot python-certbot-apache
Or, if you are using Nginx for your webserver, you can use the following command,
sudo apt-get install certbot python-certbot-nginx
Running Certbot On The Server
While logged into the server as root, you'll want to run the command certbot --apache if you are using Apache for the webserver. Otherwise, you would want to use certbot --nginx if you use Nginx for the webserver.
Please see below for a walkthrough on the first run of the certbot client.
Step One: Here, you will want to enter a valid e-mail address you can receive certificate notifications at, review and agree to the Let's Encrypt Terms of Service, and decide if you want to provide your e-mail to the Electronic Frontier Foundation (EFF) who runs the Let's Encrypt authority.
certbot --apache
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator apache, Installer apache
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): email@addre.ss
Starting new HTTPS connection (1): acme-v02.api.letsencrypt.org
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
(A)gree/(C)ancel: A
Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We want to send you an email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom.
(Y)es/(N)o:
Step Two: After that is done, the client will prompt you with a list of domains attached to the server by searching through the Apache configuration files, and it will include the hostname of the server in this list. Enter the number that corresponds with your site and press enter.
Which names would you like to activate HTTPS for?
1: hostname.hostwindsdns.com
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): 1
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for hostname.hostwindsdns.com
Waiting for verification...
Cleaning up challenges
Step Three: Once that is done, it will prompt you to ask if you want to redirect all requests to HTTPS. We strongly suggest this as it means the traffic going between the server and the visiting computer is encrypted and cannot be eavesdropped. Once you make this selection, it will update the appropriate files and install the SSL, and you're done!
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Redirecting vhost in /etc/httpd/conf.d/hwdefault.conf to ssl vhost in /etc/httpd/conf.d/hwdefault_ssl.conf
Congratulations! You have successfully enabled
https://hostname.hostwindsdns.com
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=hostname.hostwindsdns.com
IMPORTANT NOTES:
Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/hostname.hostwindsdns.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/hostname.hostwindsdns.com/privkey.pem
Your cert will expire on 2018-12-23. To obtain a new or tweaked version of this certificate in the future, run certbot again with the "certainly" option. To non-interactively renew *all* of your certificates, run "certbot renew."
If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
How is Let's Encrypt different than other Certificate Authorities?
Let's Encrypt is a new Certificate Authority and a non-profit started by industry leaders. As the new player in the space, Let's Encrypt carries with it some early limitations. Certificates will be basic encryption only – Domain Validated (DV) SSL's only confirm domain ownership by matching the email in the whois registry. They do not involve further vetting. Unlike Extended Validation (EV), the free cert will not provide the Green Address Bar, which is necessary for PCI Compliance and supporting credit card payment transactions on your website.
Written by Hostwinds Team / December 13, 2016
