Hostwinds Blog
Search results for:
What is a Proxy Server? Types, Uses, Pros/Cons & More
by: Hostwinds Team / April 3, 2024
What is a Proxy Server?
A proxy server acts as an intermediary between a user's device - such as a computer, smartphone, or tablet - and the internet. It's an extra layer of security that allows users to protect their private network and, depending on how the proxy is configured, provides anonymity when surfing the web.
How Does a Proxy Work?
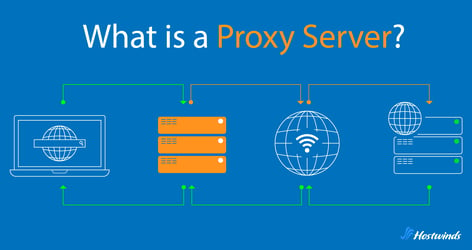
At its core, the operation of a proxy server revolves around the concept of interception and forwarding of internet traffic. There are three core components that allow this operation to work:
Client: The client refers to the user's device, such as a computer, smartphone, or tablet, that initiates requests to access the web. When the user enters a URL in their browser or clicks a link, the client sends a request to the proxy server.
Proxy Server: The proxy server is the intermediary between the client and the destination server. It sits between the client and the internet, intercepting and forwarding requests and responses between the two parties. The proxy server evaluates incoming requests, applies any configured rules or policies, and forwards the requests to the appropriate destination server. Additionally, the proxy server may cache frequently accessed content to improve performance and efficiency.
Destination Server: The destination server is the target of the client's request. It hosts the website the user intends to access. When the proxy server forwards a request to the destination server, the destination server processes the request, retrieves the requested content, and sends a response back to the proxy server.
Here's how these three components come together:
1.When a user (client) initiates a request to access a website,
2.The request is intercepted by the proxy server before it reaches the destination server.
3. The proxy server evaluates the request and forwards it to the destination server on behalf of the user.
4. The destination server accepts the proxy's request and responds to the proxy server.
5. The proxy server forwards the destination server's response (content) back to the user's device.
3 Main Types of Proxy Servers
Forward Proxy
The most common type of proxy, a forward proxy sits between the client (browser) and the internet. When a client requests website access, the forward proxy intercepts the request and, acting like a firewall, hides the client's IP address before forwarding it to the destination server on behalf of the client.
forward proxy servers are commonly used within internal networks to facilitate internet access by inspecting and filtering client requests based on the proxy server's configuration settings such as access controls and filtering policies.
Reverse Proxy
While a forward proxy works to protect clients from web servers, a reverse proxy works to protect web servers from clients. It sits in front of web servers and intercepts requests from clients, forwarding them to the appropriate backend server, shielding the servers from direct client access.
Reverse proxies are commonly used for load balancing, caching, and security, providing features such as SSL termination, DDoS protection, and web application firewalls to protect web servers from external threats.
Transparent Proxy
A transparent proxy server sits between the client and the internet, intercepting client requests similarly to a forward proxy. However, unlike forward proxies, transparent proxies do not hide the client's IP address or the fact that they are acting as a proxy server.
Transparent proxies are often used to moderate content and/or monitor users within a network without their knowledge, a practice sometimes referred to as "forced proxy."
Different Proxy Server Configurations
Anonymous Proxies
There are two levels of anonymous proxy configuration.
Level 1anonymous proxies hide the client's original IP address and doesn't inform the web server that the client request is going through a proxy.
Level 2 anonymous proxies hide the client's original IP address but will inform the web server that it is a proxy server. This is the most common proxy configuration.
Residential Proxies
Residential proxies use IP addresses assigned by internet service providers to residential users. They mimic real users' IP addresses, making them less likely to be detected as proxies by websites.
Public Access Proxies
Public access proxies are openly accessible to anyone without authentication. They provide a gateway for users to access the internet anonymously, without needing to set up their own proxy servers.
Shared Proxies
Shared proxies are used by multiple users simultaneously, allowing them to share the same proxy resources. While they offer cost savings and convenience, they may also lead to slower connection speeds and potential IP address blacklisting.
Rotating Proxies
Rotating proxies automatically rotate IP addresses with each request, providing enhanced anonymity and avoiding detection or blocking by websites. They offer dynamic IP addresses, which change regularly to disguise the user's identity.
SSL Proxies
SSL proxies perform SSL/TLS connections between clients and servers. They enable the inspection and modification of encrypted traffic, providing security and visibility into SSL-encrypted communications.
Benefits of a Proxy Server
Proxies offer numbers benefits, ranging from security to improving user experience.
Here are a few notable benefits for using a proxy server:
Security: Proxy servers add an additional layer of security by acting as a barrier between the user's device and the internet. They can filter out malicious content, detect and block malware, and prevent unauthorized access to sensitive data.
Privacy: By hiding user IPs and location, proxy servers offer anonymity across the internet, helping protect sensitive information and prevent tracking.
Network Control: From an administrative and IT perspective, proxy servers allow for a higher level of control over local networks and websites by filtering out malicious content, detecting and blocking malware, and preventing unauthorized access to sensitive data, among other things.
Performance Optimization: Proxy servers can cache frequently accessed content, reduce bandwidth usage and increase site speed. They also offer load balancing by pushing client requests to appropriate servers.
Global Reach: By connecting to a proxy server located in a different country, users can access websites and online services that are otherwise unavailable in their location.
Limitations and Challenges of Proxy Servers
While proxy servers can benefit both users and websites alike, there are a few potential drawbacks that both parties should be aware of.
Security Risks: Even though proxies are known for anonymity and security, they could potentially expose sensitive information, introduce vulnerabilities, or become targets for cyber attacks if improperly configured or compromised. Implementing proper security measures, staying on top of server updates, and regularly monitoring for suspicious activity will help ensure a proxy's security integrity.
Privacy Concerns: While proxy servers can provide anonymity and privacy, they may also raise privacy concerns if misused or abused. Some proxy servers may log user activity, including websites visited and data transmitted, compromising user privacy. It's Important to understand and evaluate the privacy policies and logging practices of proxy servers to protect user privacy rights.
Performance Impact: Proxy servers can introduce latency and impact performance, especially if they are overloaded or misconfigured. As a result, users may experience slower response times and degraded internet performance. Properly managing proxy server resources and optimizing configurations can help mitigate performance issues.
Compatibility Issues: Certain protocols, encryption methods, or authentication mechanisms may not be supported by proxy servers, leading to connectivity issues or functionality limitations. Be sure to test for compatibility with all required applications before deploying proxy servers.
Single Point of Failure: Proxy servers may represent a single point of failure in the network architecture. If the proxy goes down, it can disrupt internet access. Implementing redundancy, failover mechanisms, and backup proxy servers can help mitigate the risk of downtime and minimize service disruptions.
Proxy Server Protocols
Proxy servers can use a diverse array of protocols to accommodate just about any networking need, be it in-network or out-of-network.
HTTP Proxy
HTTP (Hypertext Transfer Protocol) proxies are designed to handle HTTP traffic specifically. They intercept and forward HTTP requests and responses between clients and servers. HTTP proxies are commonly used for web browsing and accessing HTTP-based services. They can provide features such as caching, content filtering, and access control.
HTTPS Proxy
HTTPS (Hypertext Transfer Protocol Secure) proxies are similar to HTTP proxies but specifically handle HTTPS traffic, which is encrypted using SSL/TLS. HTTPS proxies terminate SSL/TLS connections from clients, decrypt the traffic, inspect it, and then establish new SSL/TLS connections to backend servers. They provide security and visibility into encrypted traffic while preserving end-to-end encryption.
SOCKS Proxy
SOCKS (Socket Secure) proxies operate at a lower level than HTTP and HTTPS proxies. They handle various types of internet traffic, including TCP, UDP, and ICMP. SOCKS proxies create a TCP connection to a specified destination server on behalf of the client and relay data between the client and server. They are commonly used for applications such as online gaming, instant messaging, and peer-to-peer file sharing.
FTP Proxy
FTP (File Transfer Protocol) proxies are specialized proxies designed to handle FTP traffic. They intercept and relay FTP commands and data transfers between clients and FTP servers. FTP proxies can provide features such as access control, logging, and content filtering for FTP traffic.
SMTP/POP3/IMAP Proxy
SMTP (Simple Mail Transfer Protocol), POP3 (Post Office Protocol version 3), and IMAP (Internet Message Access Protocol) proxies are designed to handle email traffic. They intercept and relay email messages between email clients and email servers. These proxies can provide features such as spam filtering, antivirus scanning, and access control for email traffic.
Written by Hostwinds Team / April 3, 2024
