Hostwinds Blog
Search results for:

Reverse DNS Lookup: What is it? How Does it Work?
by: Hostwinds Team / February 8, 2024
What is Reverse DNS?
A reverse DNS (rDNS) is a domain name system that uses IP addresses to find domain names. As the name suggests, it is the opposite of the forward DNS query, which uses a domain name to locate an IP address.
What's the Purpose of Reverse DNS?
Reverse DNS helps verify the identity of a server. It's essentially a security measure used to confirm the legitimacy of a domain attempting to connect to a server. rDNS Lookups are most commonly used by email servers to authenticate message sources and filter spam.
rDNS can also be used for logging and analyzing data. By returning human-readable domain names, one can better understand their sources of incoming connections and identify potential traffic patterns or anomalies.
How Does Reverse DNS Work?
In typical DNS queries, people often trigger the process, usually through a browser. However, with rDNS queries, the initiation typically occurs in the background by servers, network devices, or automated systems.
During a reverse DNS query, the resolver specifically seeks out the PTR (Pointer) record. This record stores the DNS entries that link an IPv4 or IPv6 address to its respective host domain.
The IP addresses are stored in reverse and, depending on the IP version, appended with ".in-addr.arpa" (for IPv4) or ".ip6.arpa" (for IPv6). For example, the PTR record would store a domain with the IP address 104.168.205.10 as 10.205.168.104.in-addr.arpa.
Here are the basic steps of a Reverse DNS Query:
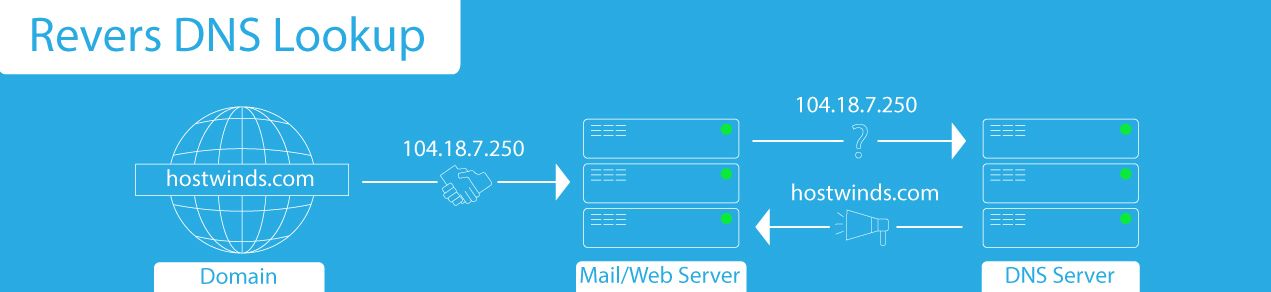
1. Server Initiates Query
A server, such as a mail server or web server, receives a request to connect from a client (ex. A domain). The server wants to verify the client's identity, so it initiates a Reverse DNS lookup by sending the client's IP address to a DNS resolver.
2. Resolver Checks Cache or Forwards Query
The resolver checks its cache for the domain associated with the IP address. If not found, it forwards the query to the authoritative DNS server. Otherwise, the resolver responds back to the server.
3. PTR Record Lookup
The authoritative DNS locates the PTR record containing the IP address queried IP address. If the record exists, the domain name found in the PTR record is sent to the resolver.
If the PTR record does not exist, the authoritative server responds with an "NXDOMAIN" (Non-Existent Domain) error code.
4. Resolver Responds to Initial Query
If the PTR record exists, the resolver sends the domain name to the server that initiated the query.
If a PTR record does not exist, the resolver will typically forward the error code information to the requesting server.
5. Server Takes Action
The requesting server verifies the domain name's association with the client IP address, typically using Forward Confirmed Reverse DNS (FCrDNS).
Perform Your Own rDNS Lookup
While reverse DNS lookups are typically handled on the backend by the server, there are a few ways you can perform your own reverse DNS lookup:
Windows
Windows command shell can be used to perform rDNS lookup using the nslookup command. Here's how that command looks:
nslookup [ip address goes here]Linux
Linux command prompt can perform rDNS lookup with the 'dig' command and '-x' flag. That command looks like this:
dig -x [ip address goes here]Online Tools
There are also a number of online tools for reverse DNS lookup. A few of the most notable:
Do You Need Reverse DNS?
Unlike forward DNS, having reverse DNS is not a strict requirement for web hosting.
However, it is highly recommended that domains are capable of rDNS lookup. Doing so allows domains to establish online trust and credibility, while also helping prevent email spoofing and improving email deliverability.
Overall, allowing your domain to accept rDNS lookups (adding PTR record to your IP address) and configuring it to perform its own reverse queries makes the internet a safer place to be.
Written by Hostwinds Team / February 8, 2024
